Battlespace Technologies: Network-Enabled Information Dominance
|
||||||||||||||||
|
Click here for the complete list of RF Cafe Quizzes. Note: Some material based on books have quoted passages.
Note: Some of these books are available as prizes in the monthly RF Cafe Giveaway. This book has some of the best photos of modern war-fighting technology that I have seen. "The era of mechanized warfare is rapidly giving way to the battle for information superiority enabled by electronic technologies that provide data for detailed analysis of enemy forces and capabilities. Supported with over 400 color photographs and illustrations, this new book is written and designed specifically to help non-specialists quickly understand the complexities of Network Enabled Capability (NEC). It offers professionals expert guidance on how to achieve information dominance throughout the battlespace by effectively employing the technologies, concepts, and decision-making processes of network enabled warfare. Written in clear, non-technical language with minimum mathematics, this book discusses how to use sensor technologies, including radar and electronic warfare systems, to disseminate information to key decision makers in timely and relevant manner..."
1. What is the most significant difference between past generations in war-fighting technology and contemporary technology? a) Nuclear weapons b) Women in the military c) Pilotless vehicles d) Information dominance
Answer: d) Information dominance It was not until the newest generation that the emphasis switched from networks and sensors as support tools to a recognition of both their centrality to warfare and the delivery of military strategy itself. (see page 3)
2. This new Network Enabled Capability (NEC), depends on which of these philosophies? a) Think globally, not locally b) Think synchronized knowledge, not synchronized requests c) Think loosely coupled flexibility, not tightly coupled efficiency d) All the above d) All the above
Answer: A 12-point list of new paradigm thinking has been adopted in the NEC philosophy. (see page 27)
3. Match the following network names to the diagrams.
(see page 65)
4. Which system provides technically derived intelligence to detect, locate, track, identify, and describe the specific characteristics of fixed and dynamic target objects and sources? a) MASINT (measurement and signature intelligence) b) HUMINT (human intelligence) c) ELINT (electronic intelligence) d) RADINT (radar intelligence)
Answer: a) MASINT (measurement and signature intelligence) (see page 119)
5. Which phenomenon is NOT a component of an aircraft's detection signature? a) Wake turbulence and aerodynamic surface heating b) Optical glint and acoustic signature c) Pilot size and weight d) Radar emissions and IR exhaust signature
Answer: c) Pilot size and weight (see page 185)
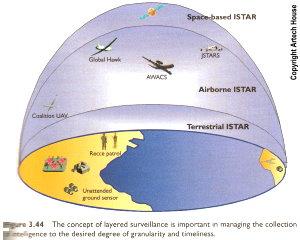
6. What is "layered surveillance?" a) Stacking of threats in order of relevance b) Using multiple generations of technologies c) Stacking physical layers of IP data d) Deploying sensors at various altitudes from ground to space
Answer: d) Deploying sensors at various altitudes from ground to space (see page 245)
7. Which markup language / protocol is fictitious? a) Microsoft Markup Language (MML) b) eXtensible Markup Language (XML) c) Transducer Markup Language (TML) d) Hyper Text Markup Language (HTML) a) Microsoft Markup Language (see page 278)
8. Long-range communications is most dependent on which parameter a) More on frequency than on power b) More on power than on frequency c) Equally on both d) Neither
Answer: a) More on frequency than on power For any given distance, time of day, and atmospheric conditions, there will be a band of frequencies the will enable optimal communications, with frequencies outside that range working poorly or not at all. (see page 296)
9. What is a primary characteristic of burst communications? a) Amplitude Modulation b) Data compression c) Quadrature modulation d) Bursts
Answer: b) Data compression Burst communications involve compressing the data and transmitting it in short bursts at unpredictable times and in an irregular pattern so that it is difficult to detect and intercept. (see page 368)
10. What is shown in the picture to the right? a) An autonomous robotic spider b) A articulately tactile sensor unit c) An inverted "dead bug" IC mounting configuration d) A Klingon spaceship
Answer: a) An autonomous robotic spider (see page 452)
Need some help? Click here for the answers and explanations.
Posted May 12, 2022 |
||||||||||||||||